The CRMLS Identity Server (OP) is implemented with IdentityServer4, an OpenID Connect and OAuth 2.0 framework for .NET. End users are authenticated via CRMLS OP that provides scope and associated claims to stem from how a client relying party (RP) is configured with custom settings per needs of each client application (e.g., based on grant type and specific requirements).
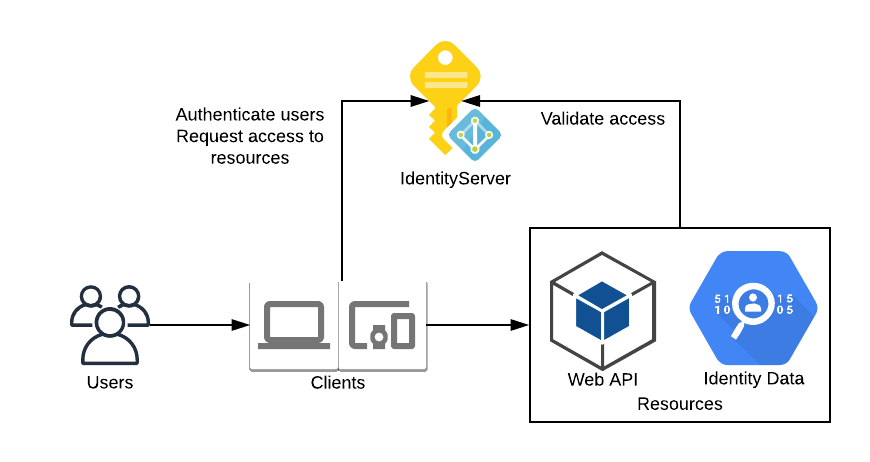
The OP protects resources such as APIs and user profile data. It authenticates users using either a local store or external IDP. It also provides session management and single sign on features to manage and authenticate clients and/or end users. The main mechanism to do this is by providing identity and access tokens that can be validated.
More on protected resources found here.
Identity Token
An identity token represents the outcome of an authentication process. It contains at a bare minimum an identifier for the user (called the sub aka subject claim) and information about how and when the user is authenticated. It can contain additional identity data.
Access Token
An access token allows access to an API resource. Clients request access tokens and forward them to the API. Access tokens contain information about the client and the user (if present). APIs use that information to authorize access to their data.
Login
The user facing login interaction is through CRMLS OP's - Identity Provider’s (IDP’s) - login page. Login through a client's own login page can also take place but that is dependent on how a client application is configured with CRMLS OP. In other words, the initial metadata the server requires provided by the client is dependent on how its configured within the system. Furthermore, the required data that a client (RP) might need also depends on how the RP is configured within the OP (i.e., client id, secret, scope and claims).
CRMLS OP Metadata
Staging: Availability: TBD
- Authority: https://socqa.crmls.org
- Configuration information: https://socqa.crmls.org/.well-known/openid-configuration
- Future login URL - TBD: https://socqa.crmls.org/Account/Login
- Logout URL: https://socqa.crmls.org/Account/Logout
Production: Availability: TBD
- Authority: https://soc.crmls.org
- Configuration information: https://soc.crmls.org/.well-known/openid-configuration
- Future login URL - TBD: https://soc.crmls.org/Account/Login
- Logout URL: https://soc.crmls.org/Account/Logout
